Are you ready to scale your enterprise?
Explore
What's New In The World of Digital.ai
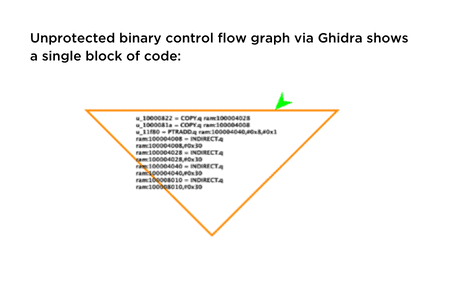
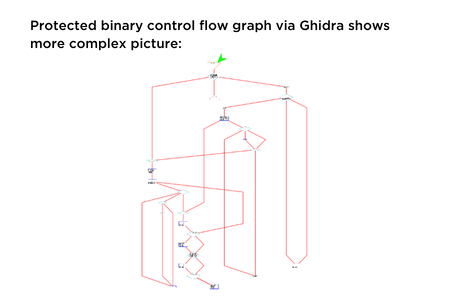
Obfuscating Code of an Android App
Learn the importance of code obfuscation on Android. Discover the benefits, tools, & best practices to protect your intellectual property and enhance security.
Summary of the CrowdStrike Incident and Prevention with Digital.ai Solutions
On July 19, 2024, a faulty software configuration update from…
Guide: How to Obfuscate Code
Learn how to obfuscate code effectively in this comprehensive guide. Discover the importance of code obfuscation and explore different types and techniques.